Mobile Security

Secure mobile with unified endpoint management (UEM)
Bring your own device (BYOD)
With over two-thirds of employees using personal devices at work, BYOD is both a boon to productivity and a security headache. Secure devices and enable authorized users to do their best work with frictionless access and an intuitive experience.
Enterprise mobility management (EMM)
Enterprise mobility means control over any type of device, whether a smartphone, tablet, laptop, desktop, or internet of things (IoT) endpoint. To improve upon MDM, EMM strives to prevent data leakage through secure containers and conditional access.
Mobile device management (MDM)
Take control of iOS, Android, macOS, Windows, and Chrome OS devices — from smartphones, tablets, laptops, and desktops to ruggedized and internet of things (IoT) endpoints. Granular device policy and remote support help customize device deployments for any use case.

JDW offers a no cost, no compromise Security Assessment
Let JDW Consulting understand your business, analyze your security environment and perform a full assessment of the security standpoint of your business that will give you peace of mind.
After our assessment we will present our results, detail any gaps found and explain our recommended plan of action
We are committed to provide the best Solutions for your Business
JDW thoroughly tests all of the solutions we represent internally before offering them to our clients. Our internal validation and use case scenario based solution validation procedures ensure that what we offer you works as the manufacturer intends it to. We make sure there will be no surprises after you invest in our offerings.
We Understand Your Needs
Our staff of professionals will understand your operations, business problems and requirements while we suggest preliminary alternatives to address them.

Propose Solutions
After our analysis, we will present you with the IBM solutions we recommend to address your needs and target the key pain points of your business.
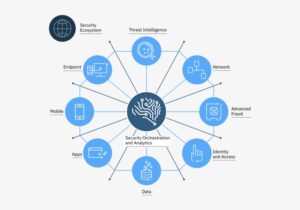
Measure Results
After the project is completed and deployed, we will assist you in measuring results, return on investment and make sure your end users are getting value out of the solutions.
Our Client's Testimonials
"JDW has been working for our Security and Access Control department for over eleven years in a multitude of projects; from identity management to threat and fraud mitigation. It would have been very complex to be able to solve most of our business problems with their expertise, guidance and fast response. Their management is top notch and present every time"
Security DirectorBank

